Most motivational methods were designed in an era where work – and workers – were different. Here we explain the science and psychology behind social employee recognition.
Social Recognition
Powerful recognition experience, diverse
reward options, meaningful engagement analytics.
A local and global solution.

Features
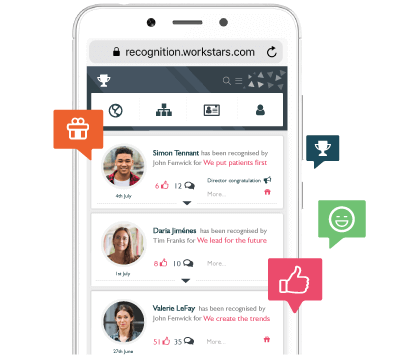
Don’t settle for One Size Fits All. Whether micro-bonuses for 50 staff or cost-of-living adjustments globally, Workstars will configure your perfect employee recognition program in a matter of minutes.
See all featuresIntegrations

With our integrations, you can share your employee recognitions with the whole company using the tools that your employees are already familiar with, including Slack, Workplace by Facebook, Microsoft Teams, Yammer and Salesforce Chatter.
IntegrateInsights
 How Machias Savings Bank improved employee satisfaction and increased commitment to company values
How Machias Savings Bank improved employee satisfaction and increased commitment to company values
Machias Savings Bank, also known as “The Bank of YES”, has been helping individuals and businesses within Maine to say “YES” to…
 Great managers vs natural leaders: What’s the difference (and does it matter?)
Great managers vs natural leaders: What’s the difference (and does it matter?)
In the world of leadership, two figures stand tall: the Great Manager and the Natural Leader. They’re not interchangeable, no matter how…
 Workstars now integrates seamlessly with the HRIS you use every day
Workstars now integrates seamlessly with the HRIS you use every day
It is now even easier to set up, launch, and manage your employee recognition program with Workstars! Our development teams have been…


